

Cloud security and compliance focus on protecting your business data, applications, and infrastructure in the cloud while ensuring all regulatory and industry standards are met. Strong cloud computing security safeguards your business from cyber-attacks, data breaches, and legal consequences due to non-compliance.
As more organizations move their operations to platforms like AWS, Microsoft Azure, and Google Cloud, the importance of reliable cloud security and aws security measures becomes critical. A secure cloud environment not only prevents threats but also builds trust with customers and partners.
Data Encryption: Protects sensitive information by encrypting it at rest and in transit, ensuring secure cloud storage.
Access Control: Restricts access using strong passwords, multi-factor authentication (MFA), and role-based access controls.
Threat Protection: Detects and neutralizes threats such as malware and ransomware with advanced cloud computing security tools.
Backup and Recovery: Ensures data is backed up regularly and can be restored quickly to maintain cloud security.
Network Security: Utilizes firewalls, VPNs, and security groups to protect against unauthorized access, especially in aws security setups.
Cloud compliance means meeting all regulatory, legal, and industry-specific requirements related to data storage, privacy, and protection. Common compliance frameworks include:
GDPR – European Union data privacy
HIPAA – Healthcare data security in the U.S.
PCI DSS – Payment card information security
ISO 27001 – Global standard for information security management
Ensuring compliance not only protects your business legally but also enhances your brand’s reputation.
Security Assessment: Identify risks in your cloud computing security setup.
Best Practices Implementation: Apply strong controls for secure cloud storage and access.
Compliance Guidance: Ensure your business meets all relevant regulations.
Continuous Monitoring: 24/7 monitoring of your cloud security posture.
Incident Response: Quickly address and resolve any aws security or data breach incidents.
Training & Awareness: Educate teams on best practices for cloud security and compliance.
Safeguards critical business and customer data
Minimizes cyber risks and breaches
Ensures compliance with laws and industry standards
Enhances customer trust and business reputation
Supports safe and secure cloud storage
Offers peace of mind through reliable cloud computing security
Completed
Task
Completed Works
with Satisfaction
Yes, different regions and industries have their own rules, so it’s important to understand which applies to you.
Regularly—ideally continuously monitored and reviewed at least quarterly to stay ahead of threats.
MFA requires users to provide two or more forms of verification (like password plus a code sent to phone) to access cloud services, adding extra security.
Begin with assessing your current setup, then apply strong access controls, enable encryption, monitor activity, and train your staff.
Services We Provide
We provide tailored solutions designed to drive growth and success. Discover how our expertise can help your business thrive.

Drive smart decisions with AI-powered insights and scalable data engineering solutions.

Infiniti TEch Solution specialize in crafting comprehensive digital marketing strategies that drive traffic, boost engagement, and increase conversions.

Scalable Azure cloud solutions to modernize, secure, and grow your IT infrastructure.

Streamline business operations with customized ERP and CRM solutions via Dynamics 365.
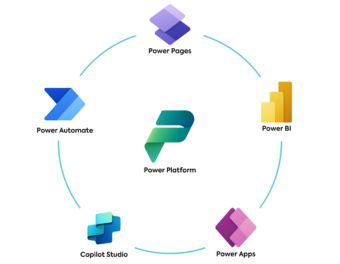
Enhance operational efficiency and accelerate innovation through a unified, enterprise-grade low-code platform.

End-to-end dairy automation for milk collection, quality analysis, billing, and reporting.

Custom Website Development We design SEO-friendly, high-performance websites that drive...
Copyright © 2025 | PREEMINENT SOFTCOM | All Rights Reserved.